Identity and Access Governance Meets Top Data Center Challenges.
For this sensitive infrastructure, only a converged solution of Cyber/IT, Physical Security and OT can provide critical, measured protection.
Take control of your data center security.


Data centers are the crown jewels of an enterprise. As companies digitally transform and global IP traffic surges, data centers have become the operational nerve center of an organization. It’s a critical infrastructure environment that needs to be highly protected—and requires a Three-Dimensional GRC (Governance Risk Compliance) and Security strategy that spans Cyber/IT, Physical Security and OT disciplines.
Data centers are complex environments that house more than systems and technologies, and as such also are part of a company’s cost center. If a server is damaged or part of a malicious threat or cyber takeover by an outsider or insider, it could mean a devastating loss to business continuity, company reputation and even ongoing profitability. Breaches or other data center compromises could also wreak drastic consequences on the business in the way of substantial regulatory fines or monetary damages.
Controlling who has access—and determining precisely how much—through full-service and automated identity, access and visitor management is a core component of effective data center security organizations. Each have different personnel, contractors, employees, visitors and even families and media entering the space. Everyone needs to be precisely tracked and accounted for in a history log that meets compliance and regulatory conformance requirements. When disparate systems and manual methods are used to provide identification and work notifications, the process becomes time consuming and error prone. This may also lead to credentials existing beyond the timeframe intended, posing additional potential security risks and compromise.
Data Center Visits and Temporary Access.
With Alert Enterprise Guardian, data center visits and temporary access can be configurable to the length of time and type of work.
Self-service portals, for managers, area owners and even contractors, reduce the burden of support for Security personnel dealing with the identity population. Real-time integration with HR systems and contractor databases further supports automated security policies and workflows.
More secure with your existing systems.
- Bulk upload and management of multiple access requests
- Manage group event requests and returning visitor checks for press, family or events
- Override access in the event of an emergency, Security or safety issue
- Auditable Security access processes
- Regulatory compliance reporting processes
- Detailed exception reporting identifies discrepancies between PIAM and PACS by flagging and highlighting events
- Vendor access for work order notification
- Training validation through integration with LMS before allowing access
According to the 2018 Cisco Annual Cybersecurity Report, nearly half of the Security risk organizations face stems from having multiple vendors and products.
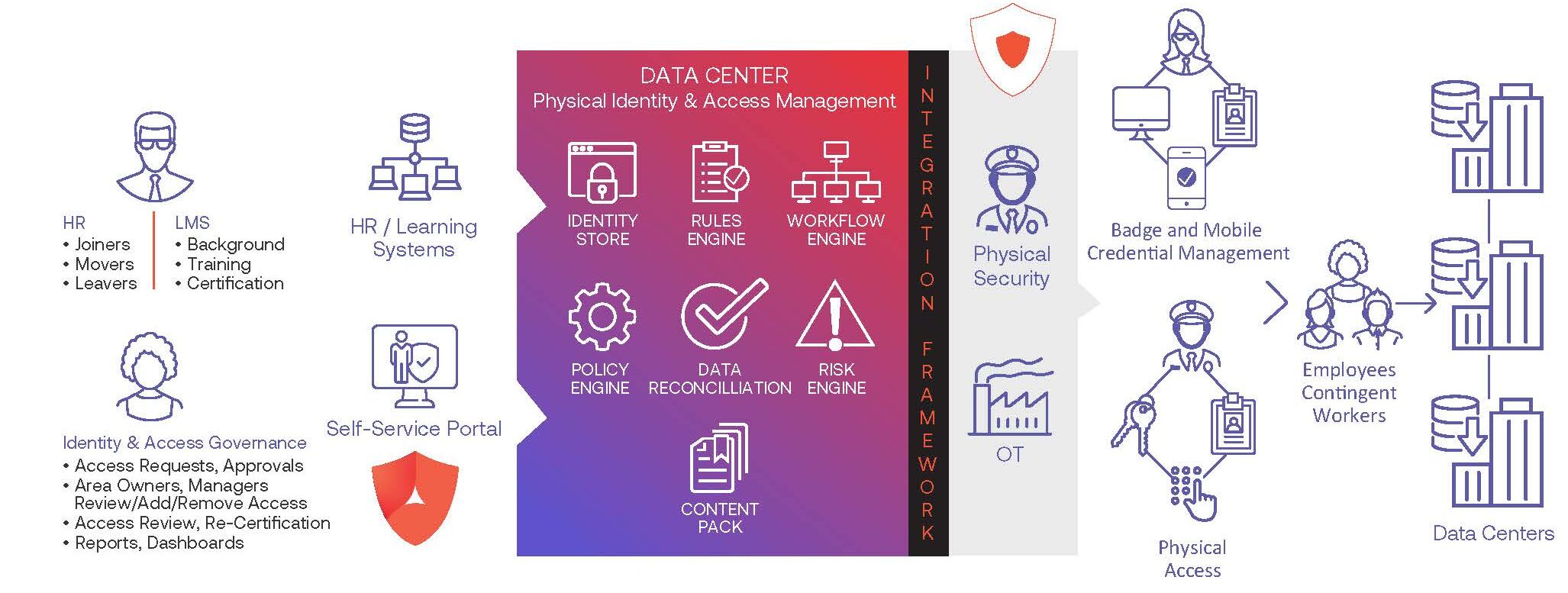
Security convergence is the answer: integrated, automated and universal digital identities deployed across IT, Physical Security and OT systems. Three-Dimensional GRC and Security solutions identify and reduce risks, close security gaps and actively enforce rules, policies and processes across the entire enterprise.
Rather than rely on different systems and processes to submit, monitor and approve access, everything happens together with a converged solution— with all movement, access and egress logged and tracked.
Data center Security solutions need to seamlessly manage all categories of identities including employees, contractors, vendors and visitors. As well as a data and intelligence driven visitor management solution to track specifics on the entire population. With Alert Enterprise, businesses can apply a standard set of Security policies across all their data centers making sure all data is safe and company-wide operational integrity is maintained.
Visitor management software pre-integrated with Physical Access Control Systems (PACS) extends the same level of protection for visitors, enforcing request approval before granting access through the enterprise-class workflow engine. Add to the mix the fact that platforms are now integrated with AI-powered Identity Intelligence technology—and users can conduct risk analysis prior to provisioning access to help proactively protect against insider threats.
What data centers need.
The Alert Enterprise platform allows data centers to automate and control exactly who has access to what critical assets. Benefits include:
- Self-service request submission and enrollment for contractors, vendors and visitors
- Enhanced Security by tracking all access requests and approvals in a centralized system
- Automated policy enforcement for training and certification integrating directly with Learning Management Systems
- Pre-integrated Physical Access Control Systems (PACS) to provision temporary access cards or badges with pre-assigned expiration dates and the ability to track locations accessed within the data center
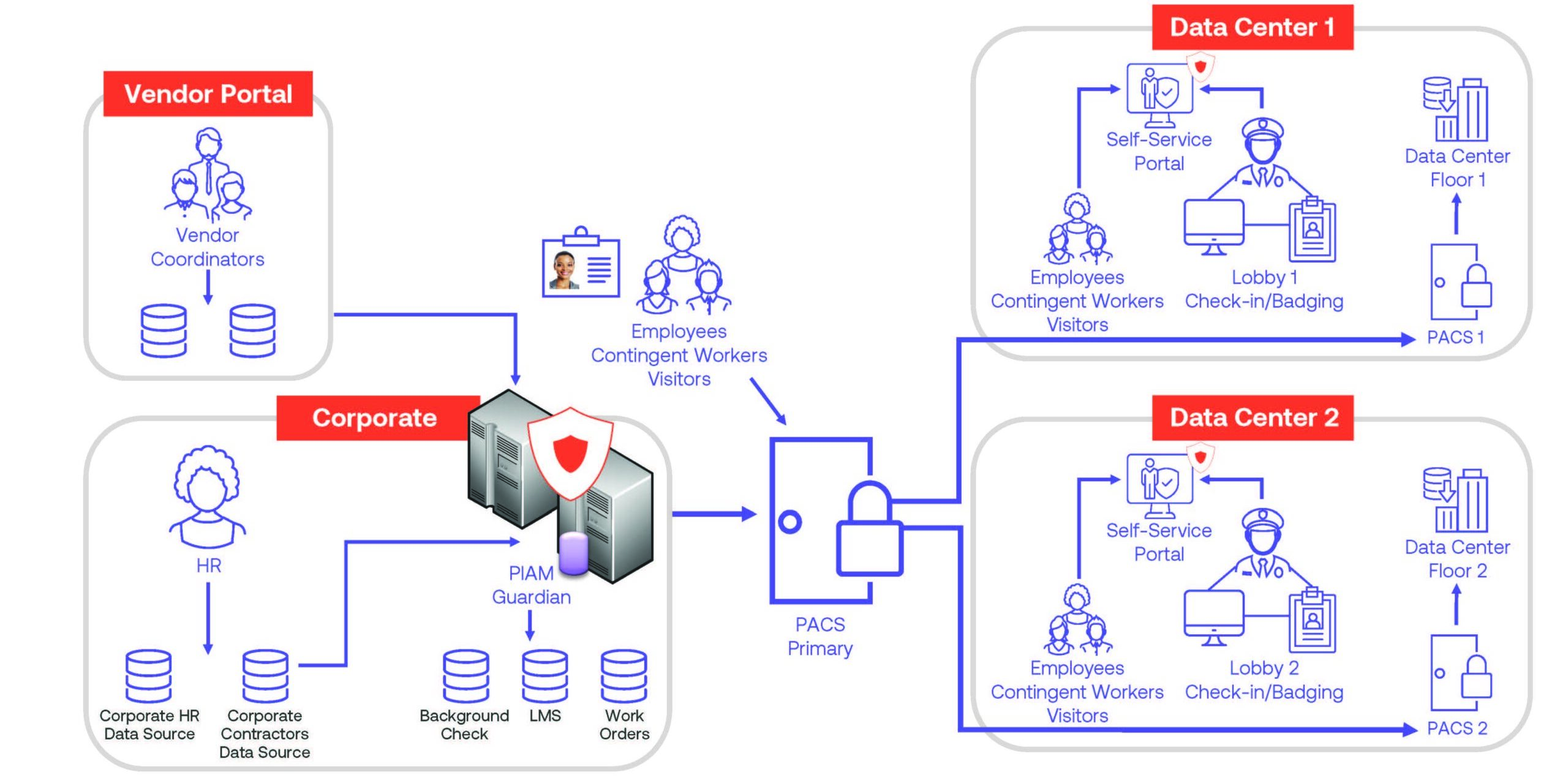
Visitor and Temporary Pass Management – Solution Architecture
The benefits of automated and converged badging and access solutions for data centers are clear:
- One-stop-shop for group visitor registration, approvals and on-demand provisioning to access controls
- Automation of conference/events visitor registration
- Capability to upload single files containing thousands of visitors
- Single interface for easy registrations, check-ins, check-outs, modified visits and badge issuance
The Alert Enterprise difference.
Alert Enterprise delivers the following benefits and features to data centers and other vertical markets:
- A common digital identity that eliminates gaps between logical and physical disciplines
- Ability to map and automate physical access rights based on specific factors such as location, employment status, threat level and compliance status
- Automated onboarding and offboarding with electronic request and approval
- Centralized physical access registration, self-service check-in, access review and authorization ticketing platform
- Robust reporting and auditing tools simplify reviewing physical access identities, access assignments and associated events in addition to automated responses
- Allows physical Security to reallocate and realign internal personnel resources and to some extent, eliminate external personnel resources for manual identity access management
- Integrates with multiple PACS (existing and future) allowing the organization to delay costly physical infrastructure and software standardization
Let’s transform.
Just think: soon, you could be up and running with the latest security automation. Ready?